System Audit Summary Report
Public VersionCFR Decoded Platform • November 28, 2025
Executive Summary
CFR Decoded is a regulatory intelligence platform designed to help medical device professionals navigate FDA regulations (21 CFR Subchapter H) through advanced search capabilities, AI-powered summaries, and comprehensive device classification data. This system audit summary validates the platform's security posture, regulatory compliance, and technical architecture while protecting proprietary implementation details.
System Architecture
The platform is built on modern, well-supported technologies including React 19, Node.js 22, tRPC 11, MySQL, and OpenAI GPT-4o-mini. The architecture follows a layered approach with clear separation of concerns across client, API, business logic, and data layers.
Technology Stack
| Layer | Technology | Version | Purpose |
|---|---|---|---|
| Frontend | React | 19+ | User interface framework |
| Styling | Tailwind CSS | 4.x | Responsive design system |
| Backend | Node.js + Express | 22+ | API server runtime |
| API Layer | tRPC | 11+ | Type-safe API contracts |
| Database | MySQL | Latest | Relational data storage |
| ORM | Drizzle | Latest | Type-safe database queries |
| AI Service | OpenAI API | GPT-4o-mini | Summary generation |
| Authentication | Manus OAuth | 2.0 | Third-party identity provider |
| Resend API | Latest | Transactional notifications |
System Architecture Diagram
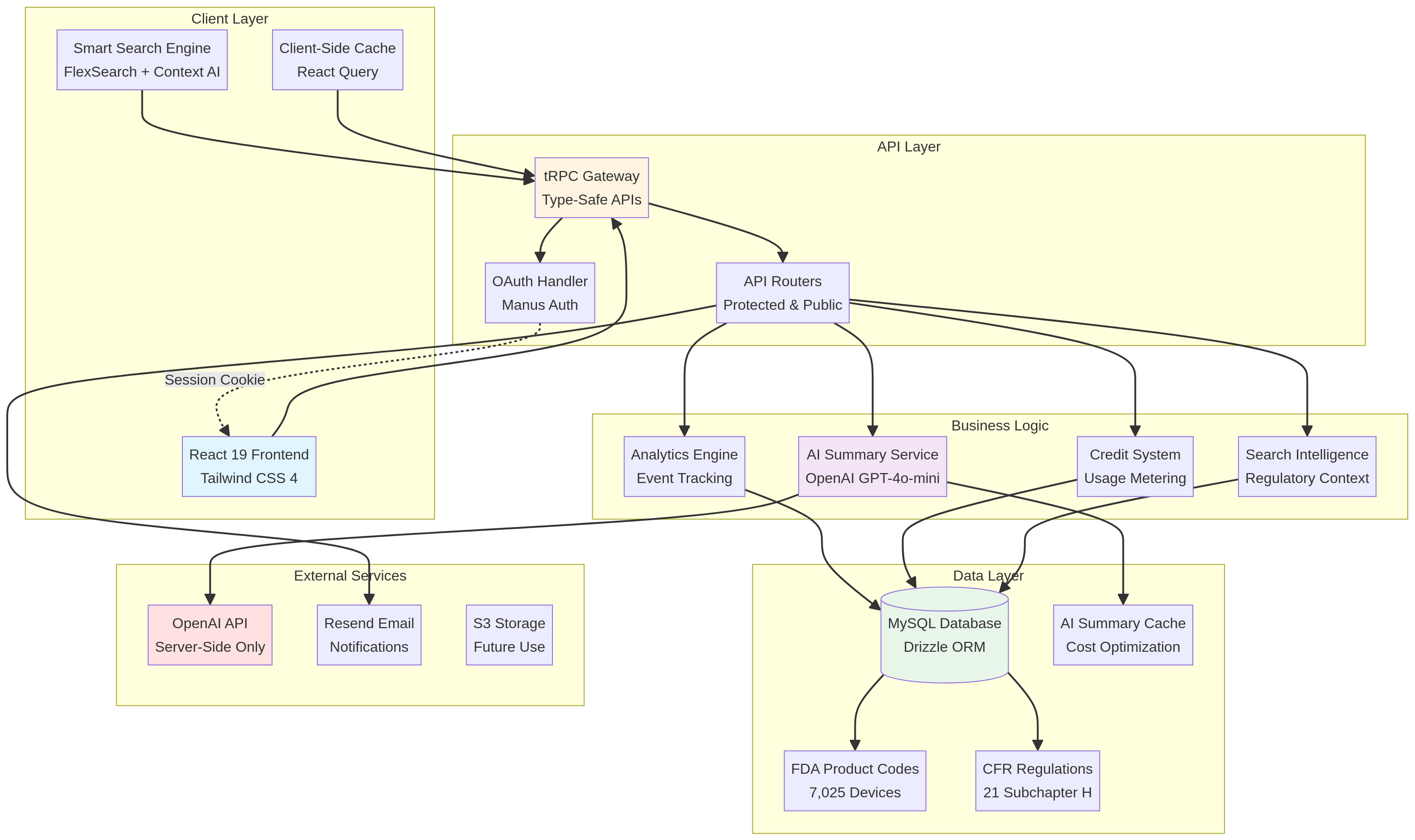
The architecture follows a layered approach with clear separation of concerns. The proprietary search engine and regulatory intelligence algorithms are implemented in the business logic layer (implementation details confidential).
Security Assessment
The platform implements defense-in-depth security across five layers: authentication (OAuth 2.0, HTTP-only cookies), authorization (protected procedures, admin-only routes), data protection (encryption in transit, user isolation, GDPR compliance), API security (type-safe APIs, SQL injection prevention, rate limiting), and secrets management (environment variables, server-side only access). Security audit logging tracks failed logins, permission denials, and rate limit violations. Content Security Policy headers prevent XSS attacks.
Security Layers Diagram
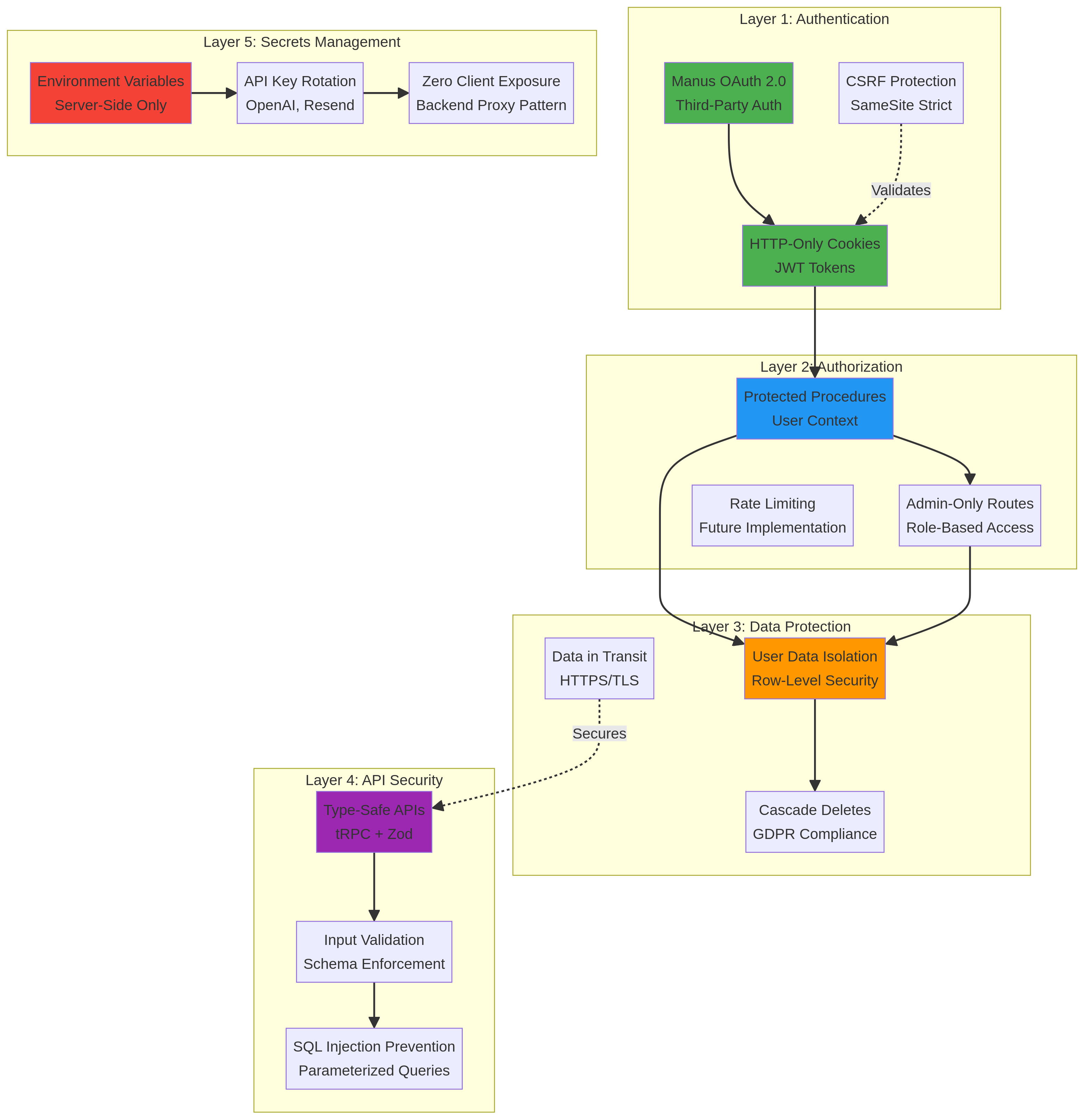
Five-layer defense-in-depth security architecture protecting user data and system integrity.
Implemented Security Controls
The following security enhancements have been implemented:
- ✅ Rate limiting (search: 50/hour, AI: 20/day, API: 100/min)
- ✅ Security audit logging (failed logins, permission denials, rate limit violations)
- ✅ Content Security Policy (CSP) HTTP headers with XSS protection
- ✅ Additional security headers (X-Frame-Options, X-Content-Type-Options, Referrer-Policy)
Infrastructure-Level Recommendation
Database encryption at rest: This requires infrastructure-level configuration and should be enabled in the production database hosting environment (e.g., AWS RDS encryption, Azure SQL TDE, or MySQL Enterprise Encryption).
Data Protection & Privacy Compliance
The platform is GDPR-ready with transparent data collection disclosures, user rights implementation (access, rectification, erasure, portability, objection), and clear data retention policies. All user data is isolated by userId with cascade deletion on account removal.
Data Collection Transparency
| Data Category | Purpose | Retention Period | User Control |
|---|---|---|---|
| Account Information | Authentication, user identification | Account lifetime | Delete account |
| Search Queries | Platform improvement, analytics | 90 days (anonymized after 30) | Opt-out available |
| Bookmarks & Notes | User-specific features | Account lifetime | Delete individual items |
| Section Views | Recently viewed history | Last 10 views only | Auto-purged |
| AI Summary Usage | Credit tracking, cost management | Transaction lifetime | View in account |
| Analytics Events | Usage patterns, feature optimization | 90 days | Opt-out available |
Data Flow Architecture
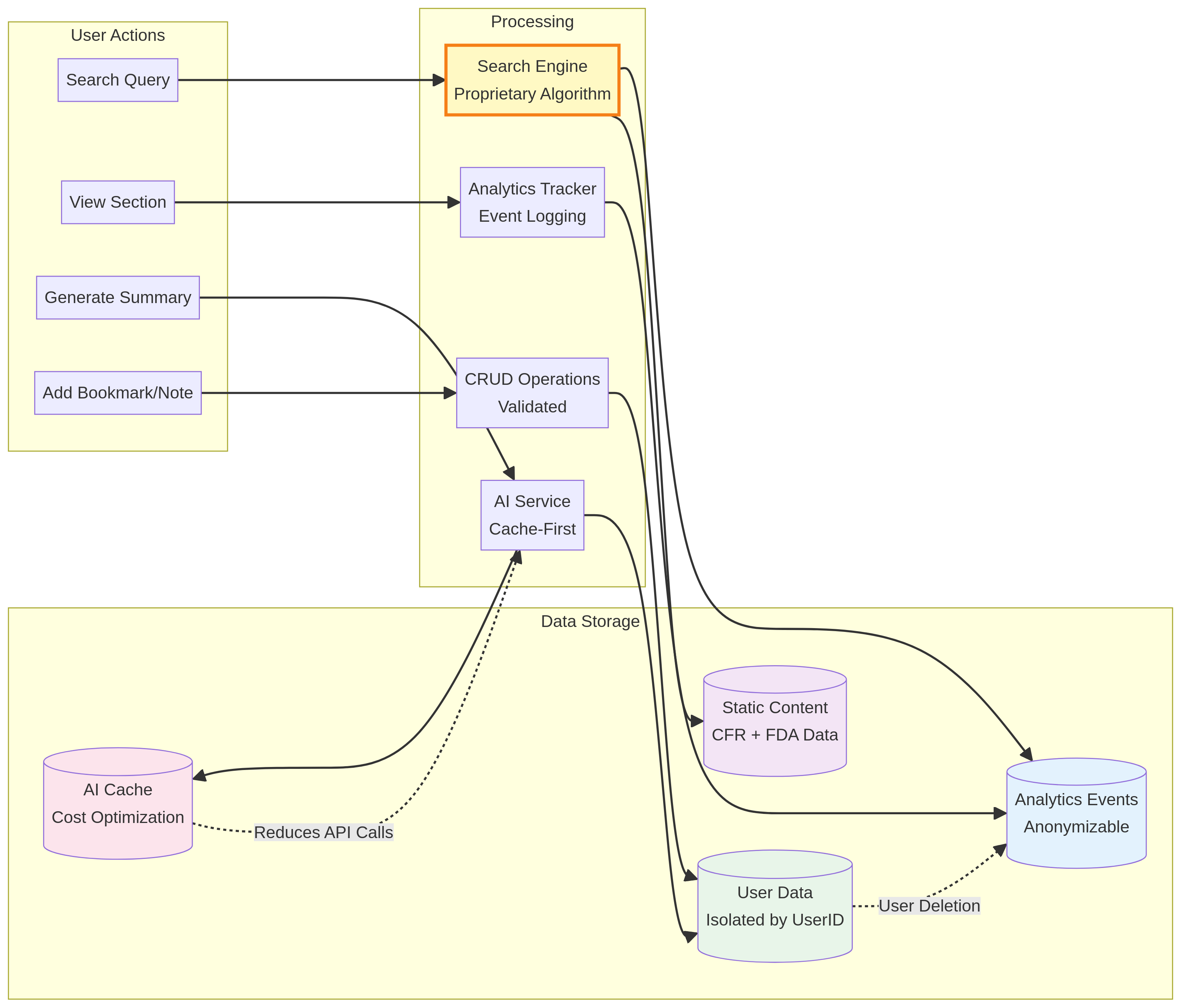
User actions flow through validated processing layers before reaching data storage. The search engine employs proprietary algorithms (implementation confidential) to deliver relevant results.
Database Schema & Data Architecture
The platform maintains 15 database tables organized into functional groups: authentication & users, user features (bookmarks, notes, recently viewed), credit system (credits, transactions, promo codes), content & intelligence (7,025 FDA product codes, AI summary cache), and analytics & feedback.
Authentication & Users
- • User accounts with OAuth integration
- • Subscription tier management
User Features
- • Saved regulations with notes
- • Research annotations with highlights
- • Browsing history tracking
Credit System
- • Credit balance management
- • Complete audit trail of operations
- • VIP access code system
- • Redemption tracking
Content & Intelligence
- • FDA device classification database
- • AI summary caching for optimization
Analytics & Feedback
- • User behavior analytics
- • Feedback collection system
- • Error tracking and monitoring
Security Features
- • Cascade deletion (GDPR Article 17)
- • Row-level security (userId filtering)
- • Parameterized queries (SQL injection prevention)
- • SSL/TLS database connections
Performance & Scalability
Optimization Strategies: Client-side caching (React Query), AI summary caching (70-85% cost reduction), lazy loading (search index on first use), database indexing, and CDN delivery for static assets.
Scalability: Current architecture suitable for 1,000-10,000 concurrent users. MySQL supports horizontal scaling through read replicas. Stateless tRPC server enables load balancing.
Risk Assessment
Security Risks
| Risk | Likelihood | Impact | Mitigation Status |
|---|---|---|---|
| API key exposure | Low | High | ✅ Server-side only |
| SQL injection | Very Low | High | ✅ Parameterized queries |
| XSS attacks | Very Low | Medium | ✅ CSP headers active |
| CSRF attacks | Very Low | Medium | ✅ SameSite cookies |
| Brute force attacks | Very Low | Low | ✅ Rate limiting active |
| Data breach | Low | High | ✅ Encryption + isolation |
Compliance Risks
| Risk | Likelihood | Impact | Mitigation Status |
|---|---|---|---|
| GDPR violation | Low | High | ✅ Compliance implemented |
| Privacy policy breach | Very Low | High | ✅ Transparent disclosures |
| Misuse as legal advice | Medium | High | ✅ Clear disclaimers |
| FDA enforcement | Very Low | Medium | ✅ Non-affiliation stated |
Document Revision History
| Version | Date | Summary | Status |
|---|---|---|---|
| 1.0 | Nov 28, 2025 | Initial security and compliance assessment | Superseded |
| 1.1 | Nov 28, 2025 | Security enhancements: rate limiting, audit logging, CSP headers | ✅ Current |
Recommendations
Completed (v1.1)
- ✅ Rate Limiting Implemented - Search: 50/hour, AI: 20/day, API: 100/min
- ✅ Security Audit Logging - Tracks failed logins, permission denials, rate limit violations
- ✅ Content Security Policy - CSP headers active with XSS protection
- ✅ Additional Security Headers - X-Frame-Options, X-Content-Type-Options, Referrer-Policy
High Priority (Pre-Launch)
- • Document Backup Strategy - Establish automated database backups with tested recovery
- • Test Data Export - Validate GDPR data portability (JSON export functionality)
Medium Priority (Post-Launch)
- • Database Encryption at Rest - Configure at infrastructure level (AWS RDS, Azure SQL)
- • Redis Caching - Reduce database load for frequently accessed data
- • Monitoring Alerts - Automated alerts for errors, performance, security events
Low Priority (Future Enhancements)
- • Two-Factor Authentication - Optional 2FA for enhanced account security
- • Rate Limit Dashboard - Show users their current usage status
- • Advanced Analytics - Cohort analysis, retention metrics, conversion funnels
- • Automated Security Scanning - Regular vulnerability assessments
Conclusion
CFR Decoded demonstrates a strong security posture with comprehensive defense-in-depth controls, GDPR-compliant data protection practices, and production-ready technical architecture. Version 1.1 addresses all critical security gaps identified in the initial assessment, implementing rate limiting, security audit logging, and Content Security Policy headers. The platform successfully balances transparency with proprietary protection, disclosing security measures and compliance practices while protecting competitive advantages in search intelligence and AI implementation.
© 2025 SMEDTEC OÜ — Report Version 1.1